Master proxytunnel to create HTTP or TCP tunnel over any proxy

When I started looking for solutions to pass any kind of flow through a proxy server I started with a premise. Proxy servers have the role of filtering user requests, protecting users from certain content and also protecting users from direct access to an unknown network.
While HTTP proxy servers play their role fully, the use of HTTPS leads to drift in the interest of the proxy itself if it is not sufficiently restricted. A client wishing to connect to a site in HTTPS, sends an HTTP CONNECT request in order to redirect the entire TLS/SSL flow to his computer. With HTTP CONNECT the client is in direct connection with the web server. And the proxy cannot know what is being shared within that connection.
- HTTP CONNECT is nothing more than a port forwarding. Proxy server can still restrict port connection and make the DNS resolution
- In case of an internet proxy, basically a user can bypass the restrictions and pass any kind of stream 😞
- For example it is possible to create SSH over HTTPS, SSH over proxy, TCP over HTTPS, TCP over proxy: encapsulate traffic through an internet proxy
The goal of this blog post it to present you two architecture and configuration in order to bypass an internet proxy, and pass traffic other than an expected HTTP. And of course... an attacker would like to hide it.
I will use here proxytunnel, because it is available on any distribution (apt-get install proxytunnel), the current version is stable (binary release in 2008-2012 depending on the version) and and it can interact with several proxy configurations. In this post I will focus on routing SSH protocol but it will work on any TCP based protocol.
Two architectures presented bellow is:
1️⃣ > Proxy in proxy
2️⃣ > SSL tunnel and multiplexer
Proxy in proxy
Create SSH tunnel across one local proxy and one remote proxy
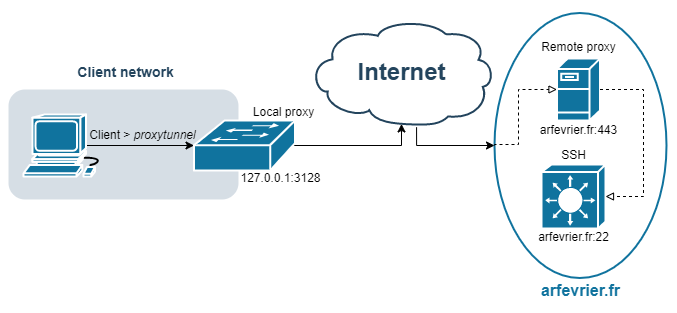
Proxy in proxy is in my opinion the best way and implementation to route and hide TCP trafic. We only need to setup a remote proxy. And this remote proxy can be implemented with apache2 or nginx!
Because the remote proxy is accessible from internet we need to protect it. I will use basic authentication (username/password). We want an HTTPS proxy on port 443, so the local proxy cannot spy the request from the client. This the apache2 configuration I use for remote proxy:
Connection step realized by proxytunnel in the SSH config:
- Client request an CONNECT arfevrier.fr port 443 on local proxy
- Client request an CONNECT arfevrier.fr port 22 on remote proxy
- The SSH port is opened, SSH key exchange start
-p for local proxy, -r remote proxy, -R for the basic authentification and finaly -X to tell proxytunnel that the connection to the remote proxy is TLS/SSL encrypted (HTTPS ).
SSL tunnel and multiplexer
Create SSH tunnel with SSL encapsulation and hide SSH server
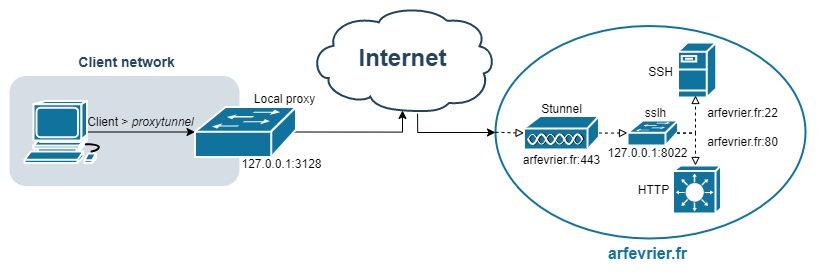
Description and configuration to connect to SSH server, in case you can't directly connect using SSH (port 22) protocol. The idea is to use a proxy with HTTP CONNECT capability to transmit SSL/TLS which, does not encapsulate HTTP, but encapsulate SSH.
Why sslh ?
sslh is just here to make valid HTTP response in case of HTTPS request on the port 443 of the server. This is optional. But without this, request on port 443 will result by weird HTTP/0.9 response from sshd.
- Stunnel: The stunnel program is designed to work as an SSL encryption wrapper.
- sslh: An Applicative Protocol Multiplexer, "accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client."
Here is a docker-compose file which will help you to setup the Stunnel and sslh:
Finally the ssh config file to use in order to connect to Stunnel using the local proxy. In the proxytunnel command, we specify the parameter -e to tell that paquet between client and stunnel is TLS/SSL encrypted.
Source code, installation and script of this post can be found on my Github:


